We'll integrate CentOS 7 (File Server) with Windows Active Directory using winbind + Samba
Domain: SA
AD FQDN: sa.local
DC FQDN: dc2.sa.local
CentOS 7 FQDN: centos7.sa.local
Start off with a CentOS 7 minimal install. I used VM Workstation 10.
Configure a hostname "centos7.sa.local" and set a static IP address.
Be sure /etc/resolv.conf points to the AD as the nameserver.
Copy and paste below commands in CentOS 7 using root login.
Domain: SA
AD FQDN: sa.local
DC FQDN: dc2.sa.local
CentOS 7 FQDN: centos7.sa.local
Start off with a CentOS 7 minimal install. I used VM Workstation 10.
Configure a hostname "centos7.sa.local" and set a static IP address.
Be sure /etc/resolv.conf points to the AD as the nameserver.
Copy and paste below commands in CentOS 7 using root login.
# Centos 7.x fileserver with AD authentication of users :: revision 5/1/2015
#
#
#—— turn off the firewall
systemctl stop filewalld.service
systemctl disable firewalld.service
systemctl stop filewalld.service
systemctl disable firewalld.service
#—— check selinux status and turn off as necessary
sestatus
# vi /etc/selinux/config and change to selinux=disabled
sestatus
# vi /etc/selinux/config and change to selinux=disabled
#—— install auxillary packages — these will be useful
yum -y install ntp
yum -y install bind-utils
yum -y install net-tools
yum -y install ntp
yum -y install bind-utils
yum -y install net-tools
#—— verify Centos can resolve the AD server
nslookup dc1.sa.local
nslookup dc1.sa.local
#—— verify Centos can reach the AD server
ping dc1.sa.local
ping dc1.sa.local
#—— setup time syncronization to the AD — set the server pool to include the AD
vi /etc/ntp.conf
# add the AD server to the ntp server pool, e.g., server dc1.sa.local
vi /etc/ntp.conf
# add the AD server to the ntp server pool, e.g., server dc1.sa.local
#—— create the home directory for the domain users — note name capitalization
mkdir /home/SA
chmod 0777 /home/SA
mkdir /home/SA
chmod 0777 /home/SA
#—— install the necessary packages
yum -y install samba samba-winbind*
yum -y install authconfig-gtk*
yum -y install samba samba-winbind*
yum -y install authconfig-gtk*
#—— verify the time can be pulled from the AD server
net time -S dc1.sa.local
net time -S dc1.sa.local
#—— sync the time to the AD server
net time set -S dc1.sa.local
net time set -S dc1.sa.local
#—— start and enable the services to run at boot time – ntpd, smb, winbind
systemctl start ntpd
systemctl enable ntpd
systemctl start smb
systemctl enable smb
systemctl start winbind
systemctl enable winbind
systemctl start ntpd
systemctl enable ntpd
systemctl start smb
systemctl enable smb
systemctl start winbind
systemctl enable winbind
#—— verify that ntpd, smb, and winbind are indeed enabled to start at boot time
systemctl list-unit-files –type=service | grep enabled
systemctl list-unit-files –type=service | grep enabled
#—— setup winbind authentication
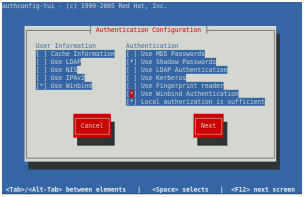
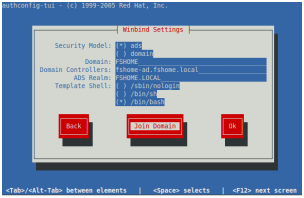
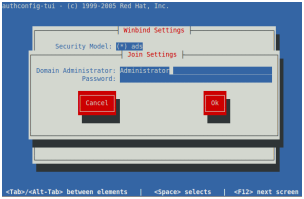
authconfig-tui
authconfig-tui
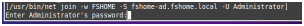
#—— configure as shown in the following graphics
#—— ignore the “No DNS name configured…” error after entering the password
#—— verify domain join
net ads testjoin
net ads testjoin
#—— verify AD server info
net ads info
net ads info
#—— verify users are pulled from AD
wbinfo -u
wbinfo -u
#—— verify groups are pulled from AD
wbinfo -g
wbinfo -g
The listing will show the output as DOMAIN/username. Same with the groups. So to fix that
#—— remove the DOMAIN prefixes from the users and the groups
authconfig --enablewinbindusedefaultdomain --update
authconfig --enablewinbindusedefaultdomain --update
#—— verify the DOMAIN prefix no longer exist
wbinfo -u
wbinfo -g
wbinfo -u
wbinfo -g
###
### on the AD server run the dsquery * command to verify the
### Centos results correspond to AD
### for granularity run the following: dsquery ou, dsquery group, dsquery user
###
### on the AD server run the dsquery * command to verify the
### Centos results correspond to AD
### for granularity run the following: dsquery ou, dsquery group, dsquery user
###
#—— allow autocreation of home directories from ssh users login
authconfig --enablemkhomedir --update
authconfig --enablemkhomedir --update
#—— allow auto-creation of home directories from Windows clients login by using a script for same
# create script as shown below-
touch /usr/local/sbin/mkhomedir.sh
vi /usr/local/sbin/mkhomedir.sh
# create script as shown below-
touch /usr/local/sbin/mkhomedir.sh
vi /usr/local/sbin/mkhomedir.sh
——————— script start ———————–
#!/bin/bash
#!/bin/bash
if [ ! -e /home/FSHOME/$1 ]; then
mkdir -m 0700 /home/FSHOME/$1
chown $1:”domain users” /home/FSHOME/$1
fi
exit 0
———————– script end ———————–
mkdir -m 0700 /home/FSHOME/$1
chown $1:”domain users” /home/FSHOME/$1
fi
exit 0
———————– script end ———————–
#—— set script permission
chmod u=rwsx,g=rwx,o=rwx /usr/local/sbin/mkhomedir.sh
chmod u=rwsx,g=rwx,o=rwx /usr/local/sbin/mkhomedir.sh
#—— verify the script permissions
ls -l /usr/local/sbin/mkhomedir.sh
ls -l /usr/local/sbin/mkhomedir.sh
Now need to make changes to the default Samba configuration in the [homes] section…
#—— setup smb.conf [homes] section
vi /etc/samba/smb.conf
vi /etc/samba/smb.conf
[homes]
comment = Home Directories
…
inherit permissions = yes
root preexec = /usr/local/sbin/mkhomedir.sh %U
comment = Home Directories
…
inherit permissions = yes
root preexec = /usr/local/sbin/mkhomedir.sh %U
#—— reboot Centos
sync;reboot
sync;reboot
#—— verify configuration still holds after reboot
net ads testjoin
net ads info
wbinfo -u
wbinfo -g
net ads testjoin
net ads info
wbinfo -u
wbinfo -g
#—— login from a Windows workstation and verify the user’s directory is automatically created, and files can be added and deleted
Go to Run>Type "\\centos7.sa.local\" and hit enter
Put domain user's credentials to login.
#—— Have Fun!
####
### tools/notes for reference
###
### tools/notes for reference
###
#—— dump a list of the autoconfig settings
authconfig –test > authconfig.txt
authconfig –test > authconfig.txt
#—— change the host name
hostnamectl set-hostname centos7.sa.local
hostnamectl set-hostname centos7.sa.local
#—— if the fileserver hostname is changed, rerun authconfig-tui to rejoin the domain with the new hostname
#—— to restart the network interfaces
systemctl restart network.service
systemctl restart network.service
#—— show the IP address on the interface(s)
ifconfig
Ref:
https://theserverplaypen.wordpress.com/2015/05/25/integrating-centos-7-with-active-directory-using-winbind/
ifconfig
Ref:
https://theserverplaypen.wordpress.com/2015/05/25/integrating-centos-7-with-active-directory-using-winbind/